Users and roles#
Like most DBMS-es Querona uses users and roles for access management. Permissions can be assigned on a per-user or per-role basis.
Any number of users can be assigned to a single role.
The following chapter describes the user, role and permission management.
User management#
This section can be found under :
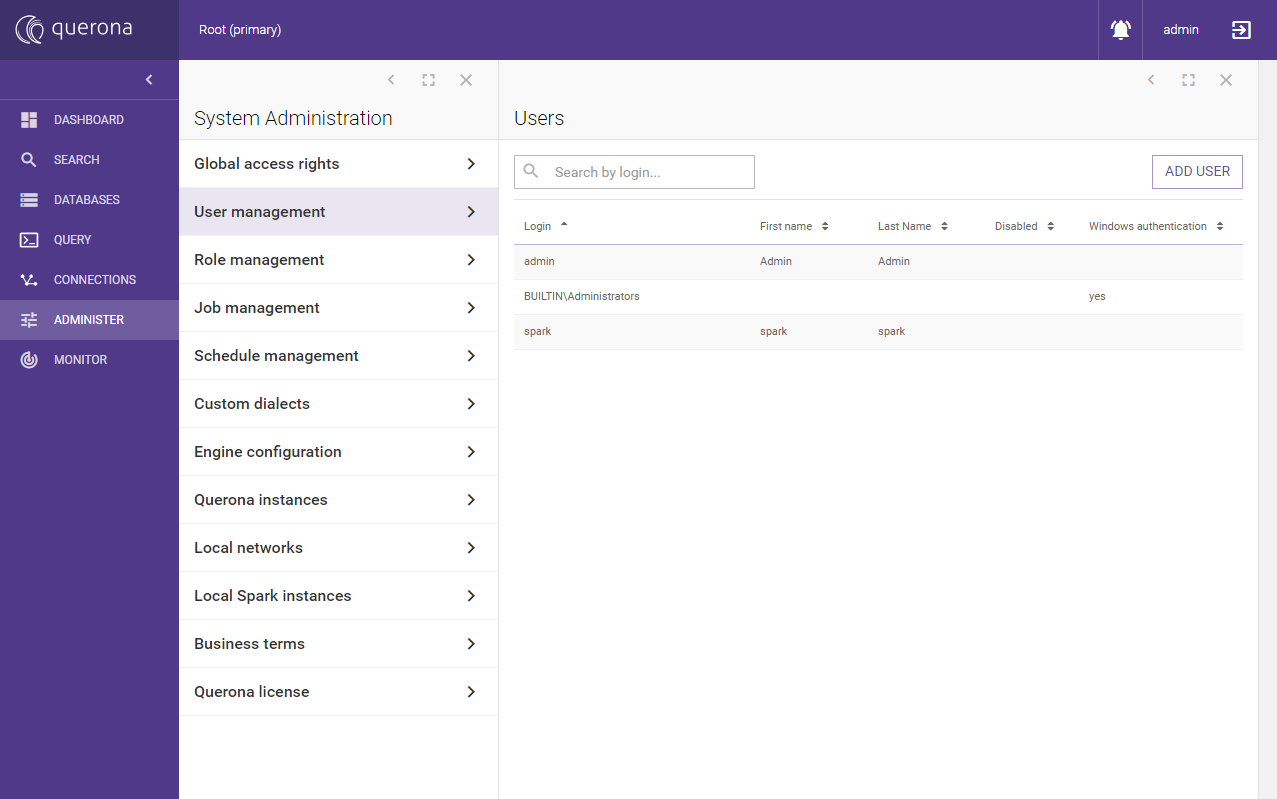
Querona comes with a predefined user accounts:
Account name |
Description |
|---|---|
admin |
The default administrative account |
spark |
The default account used for reverse Spark connections (see: Managing Apache Spark) |
BUILTIN\Administrators |
Default Windows Administrators group mapping |
system (hidden) |
The default system account used by Querona |
A new user can created using the Add user button:
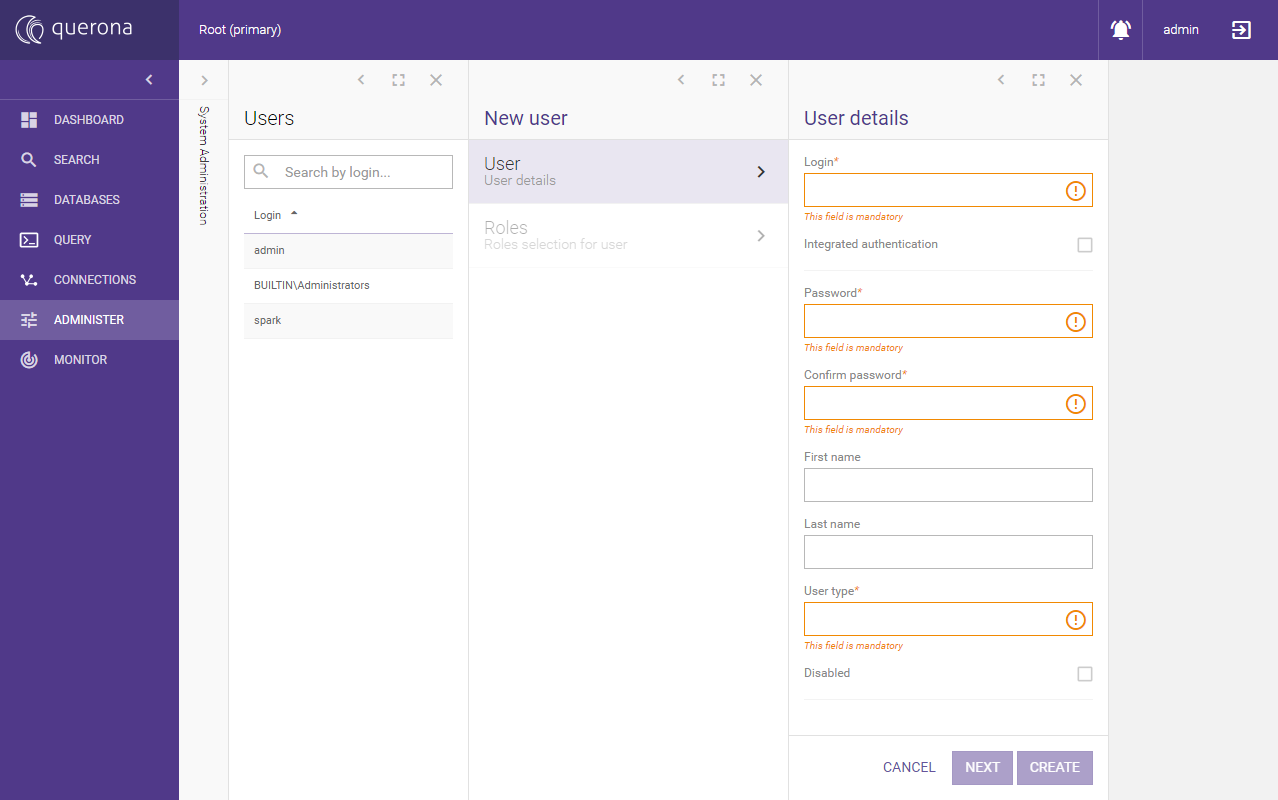
The following table summarizes the fields:
Field name |
Description |
|---|---|
Login |
The name of the account. If using Windows Authentication, the format should be “DOMAIN\account”. |
Integrated authentication |
Enabled Integrated Windows Authentication, disables password |
Password |
Account password when using SQL authentication |
Confirm password |
Retype password |
First name |
Optional: user’s first name |
Last name |
Optional: user’s last name |
User type |
Type of the account: Regular - standard account, Spark reverse account - see: Managing Apache Spark, System - reserved for system account - do not use |
Disabled |
Disabled accounts are rejected on authentication |
The next screen allows assigning the account to Roles. Every account must be assigned at least to public role.
Once defined, you can use the Access rights functionality to define the actual permissions for the given user.
Role management#
This section can be found under :
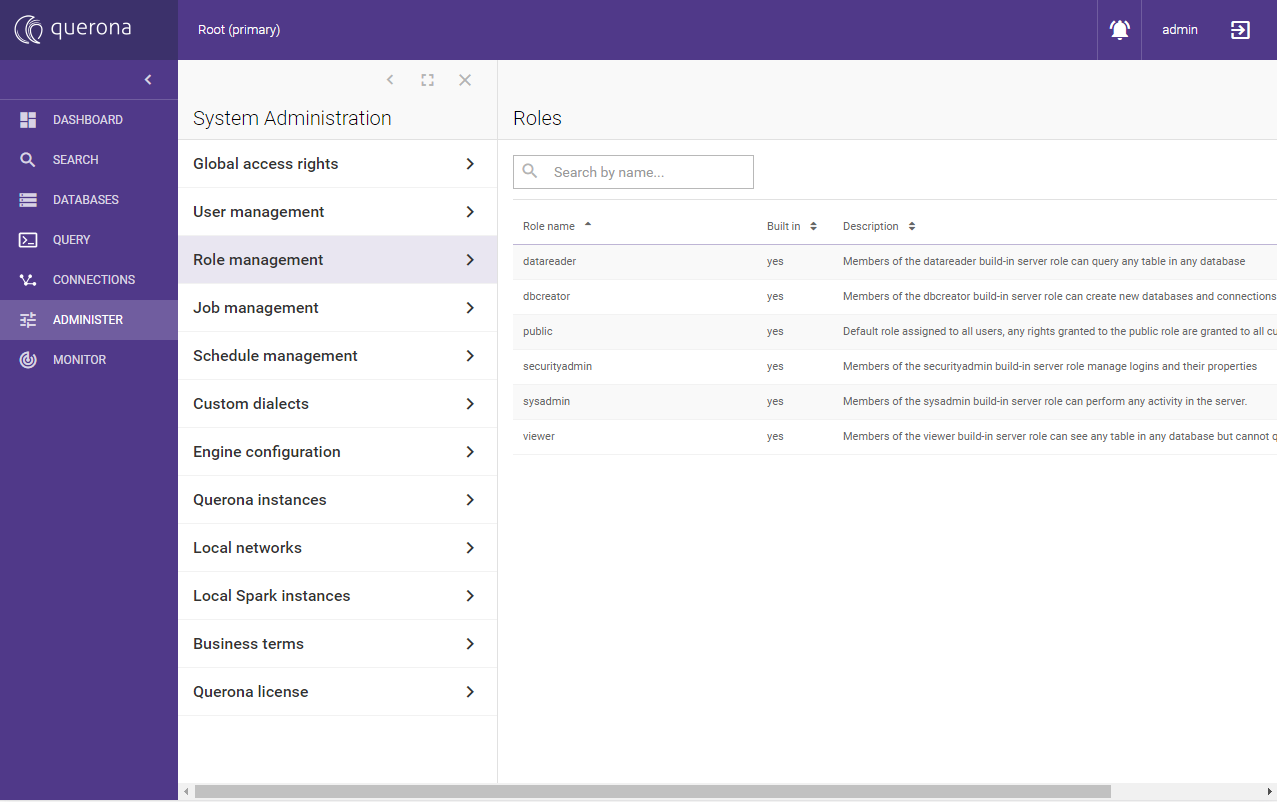
Querona comes with several predefined roles:
Role name |
Description |
|---|---|
datareader |
Members of the datareader built-in server role can query any table in any database |
dbcreator |
Members of the dbcreator built-in server role can create new databases and connections |
public |
Default role assigned to all users, any rights granted to the public role are granted to all current and future users |
securityadmin |
Members of the securityadmin built-in server role manage logins and their properties |
sysadmin |
Members of the sysadmin built-in server role can perform any activity in the server. |
viewer |
Members of the viewer built-in server role can see any table in any database but cannot query or modify data |
A new role can created using the Add role button:
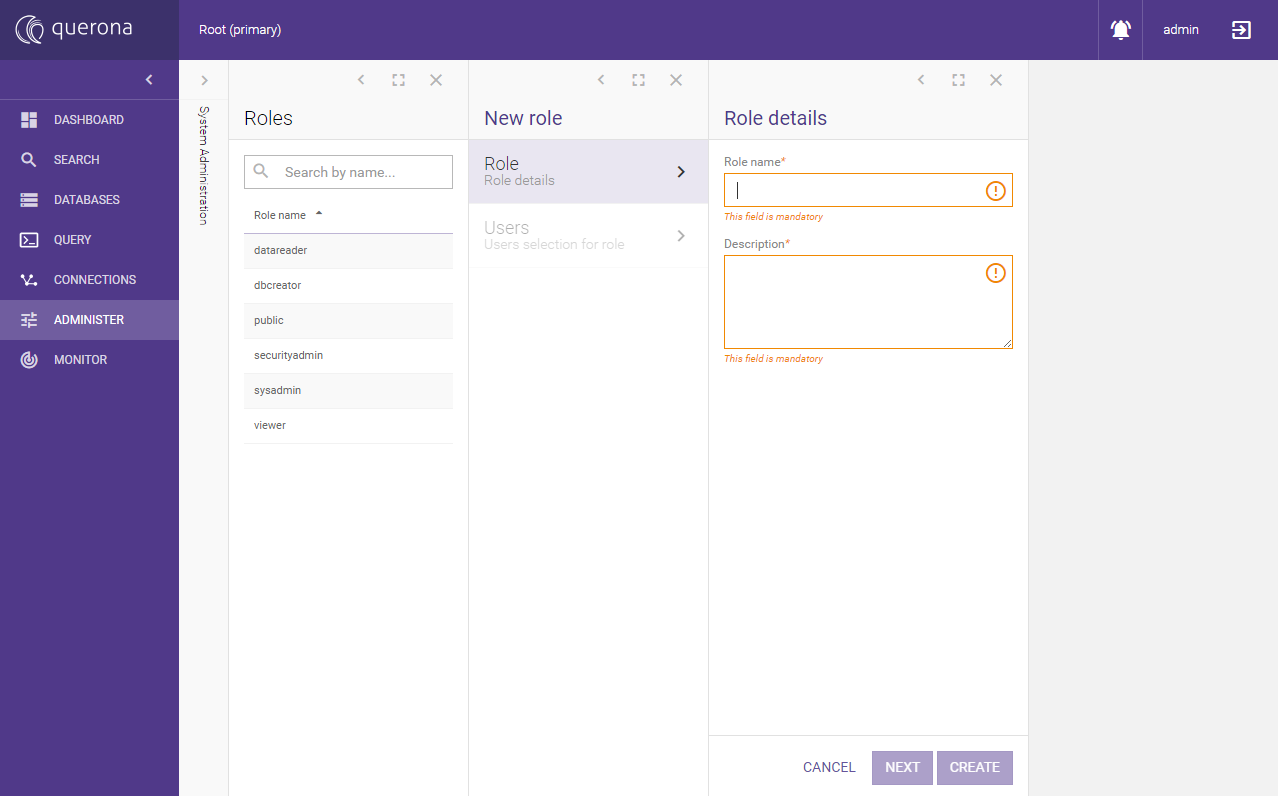
The subsequent screen allows adding any existing user to the newly created role.
Once defined, you can use the Access rights functionality to define the actual permissions for the given role.
